
Cybersecurity goals and challenges in 2023…and beyond!
We take security seriously —with offerings like Parallels RAS and Parallels Awingu providing secure remote access to virtual apps and desktops, as well as internal resources.
Recently, we partnered with Qualtrics to survey nearly 500 IT professionals who are responsible for cybersecurity at large international companies. The goal? Get a better understanding of the current state of cybersecurity at world class organizations and see what their main goals and challenges are right now and in the future.
8 out of 10 companies make security a top priority
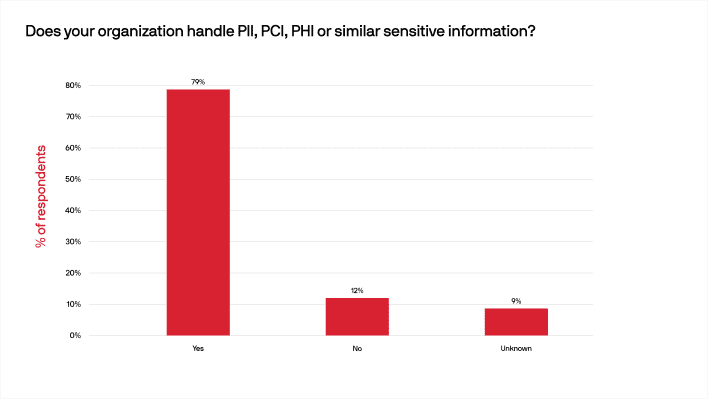
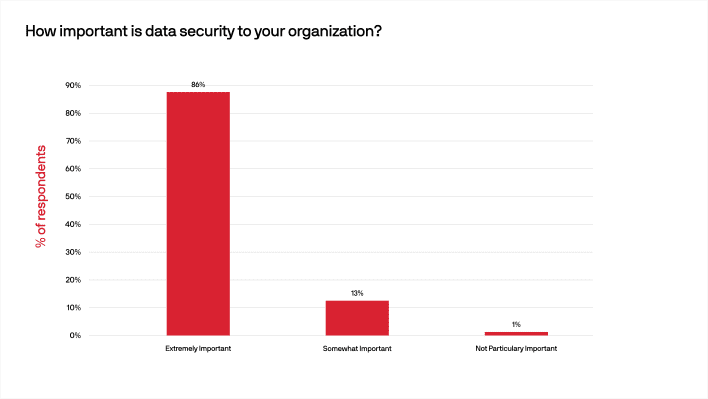
79% of respondents reported that their organization works with personally identifiable information (PII), payment card information (PCI), or personal health information (PHI). So, it is not surprising that the significant majority — 86% — of those surveyed reported that security was extremely important at their companies.
Malware and ransomware attacks are primary concern, followed by cloud vulnerabilities
While most of their respondents rated their current security as at least adequate, 64% reported that malware and ransomware attacks were the primary concern for external threats. While that information is not unanticipated considering the prevalence and awareness of these threats, what is particularly intriguing is that 42% of respondents reported that cloud vulnerabilities were second on the list of security threats with outside origins.
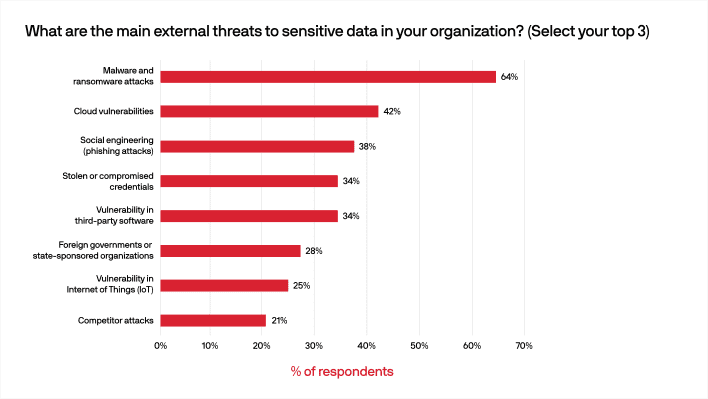
With cloud adoption growing in popularity at an astonishing rate, it only goes to follow that savvy security and IT professionals are taking security in the cloud into account. Social engineering and stolen or compromised credentials were also prominent concerns, as well as internal threats like various types of human error like weak passwords or employee negligence.
Ensuring data security by means of zero-trust architecture (ZTA)
The threats detailed above and the other responses we gathered in this survey underscore the value and necessity of a zero-trust approach in today’s world. ZTA–which operates under the principles that all entities are untrusted by default, least privileged access is enforced, and comprehensive security monitoring is implemented- is a core foundational requirement of secure remote access.
ZTA works on the principle of “trust is good, control is better”. Regardless of where the request comes from or to which source it is directed, every access request is treated as potentially dangerous and comprehensively checked before access is granted. This makes the zero trust approach a powerful, flexible and granular way to control access to data across an organization’s IT, network and security landscape.
Rising security investments in 2023
With all the potential security threats out there, we also weren’t shocked to see that organizations plan to increase their security expenditures, with 78% total reporting they planned to up their security budgets moderately or significantly in the coming year.
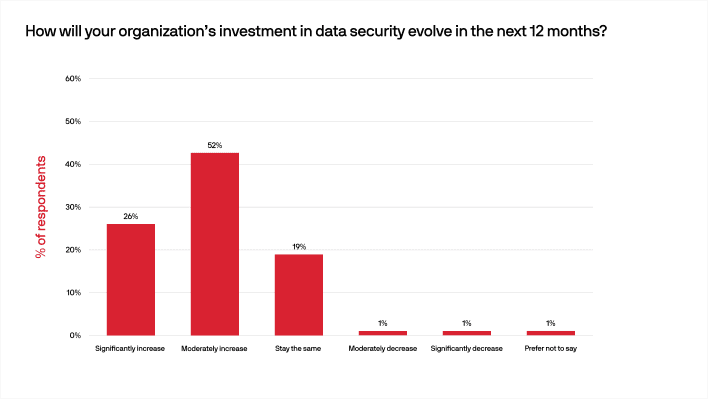
This may or may not be connected to the rapid adoption of the cloud or how remote work is here to stay.
Unfortunately, it is all too common that IT organizations have been impacted by some type of cybersecurity event, often related to cloud vulnerabilities and/or remote access. So, there’s no denying the fact that IT professionals are putting cybersecurity at the forefront of their minds — and budgets.
Vast majority of companies have high confidence in their security solutions
Despite all the internal and external threats organizations are facing, there was a certain amount of confidence exhibited by our respondents, with 64% stating that they did not expect a security breach in the coming twelve months and 59% saying they did not experience a security breach during the previous year.
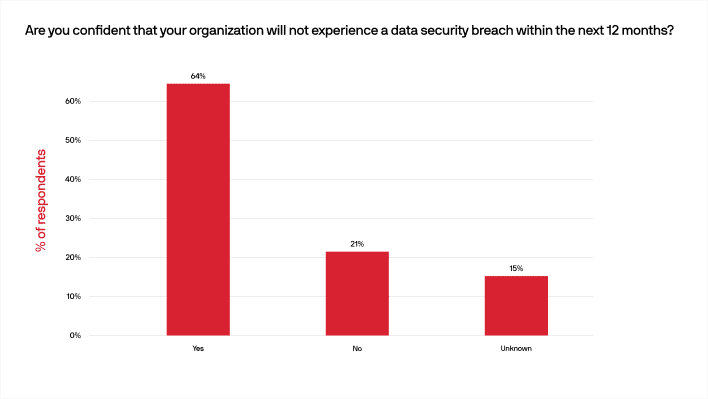
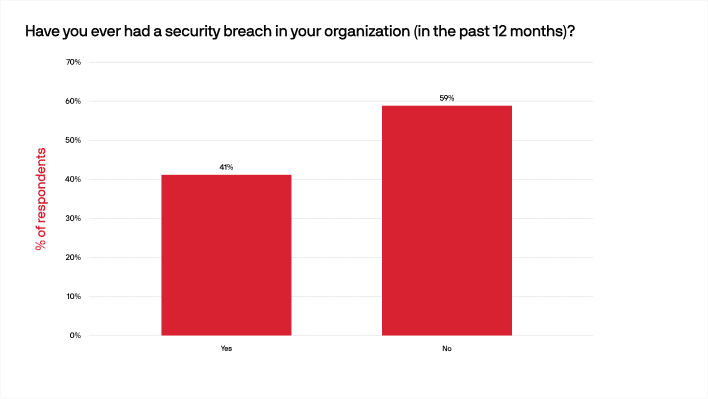
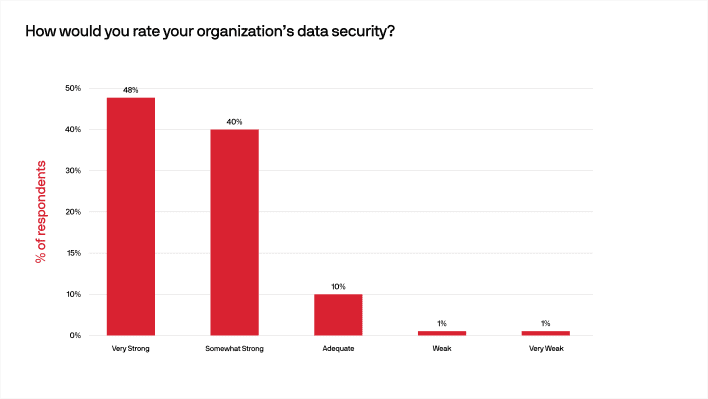
This confidence could be the result of having proper security solutions in place, since 88% of respondents reported their current security solutions are either very strong or somewhat strong (as opposed to adequate or less). With today’s reality of hybrid and remote work, a secure solution for accessing work applications regardless of their location is critical.
How we performed this cybersecurity study:
Want more details? We used Qualtrics’s research tools and communities to gather a sample of professionals who are responsible for or involved in the cybersecurity for their organizations. The survey was completely anonymous, and respondents were not aware that it was funded by Alludo in late Q1, 2023.
Interested in learning more? Contact us or access the full report!


