We’re proud to announce another major achievement in our unending quest to provide only the best products for our customers. Parallels® Remote Application Server (RAS) recently won a 2020 TrustRadius Top Rated Award in the...
This article covers the basics of SAML authentication, how it works behind the scenes, the benefits of using SAML authentication and how it streamlines user access to your organization’s applications.
What is SAML...
Many companies are now realizing that there are advantages to having their employees work remotely, including better competitiveness and lower operating expenses. During the COVID-19 pandemic, an effective...
Remote workforce management: There’s no doubt that remote work has become the new normal. Businesses have come to realize how adopting a remote work strategy enables employees to become more attuned to their job, less susceptible...
What Is Citrix Systems?
Citrix Systems provide remote access and virtual computing solutions, among others. From its humble beginnings in the late 1980s, Citrix has grown to become a major player in the...
System console and the challenges of using multiple system consoles
A system console (also called the computer console, root console, or operator’s console) is the text entry and...
What Are Mobile Apps?
Mobile apps are designed to run on mobile phones and tablets, among other compact devices. They remain as popular as ever, powered by growing demand for increasingly capable,...
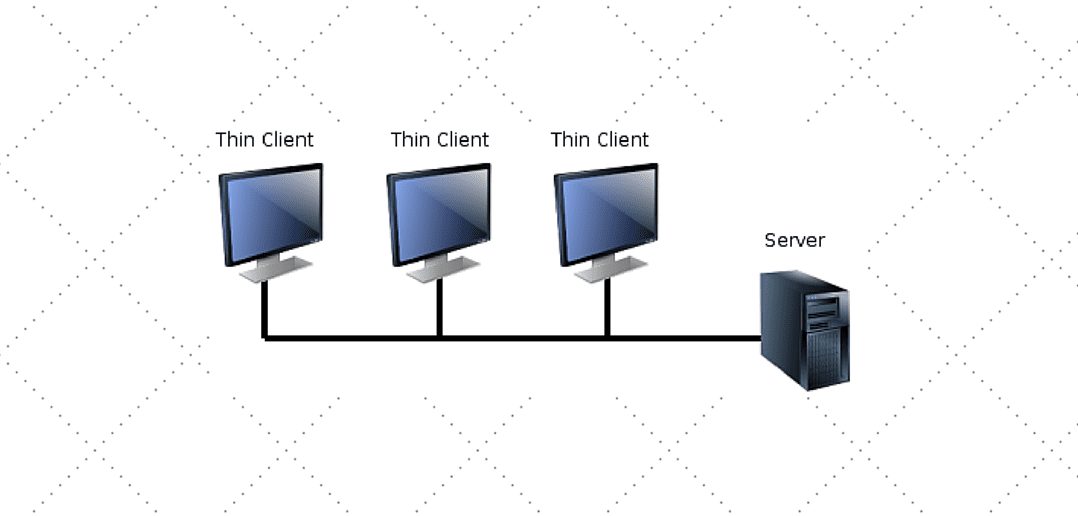
Common Problems with Citrix Thin Clients
Problem with Citrix thin clients. Citrix thin clients are susceptible to a wide range of problems. Some of the most common include:
Citrix logon page fails to...