Microsoft recently announced the end of support for Windows 10, and users are encouraged to make the transition to Windows 11 sooner rather than later.
From the official statement on the Windows 10 product page, “Windows...
In the fast-paced world of modern business, the surge in natural disasters, intensified by climate change, poses unprecedented business challenges.
Businesses must be ready for anything,...
Over the past decade, there has been an undoubted shift towards companies adopting and efficiently managing their applications and data in the cloud. However, this rush towards the cloud has left many companies with more complexity within their IT...
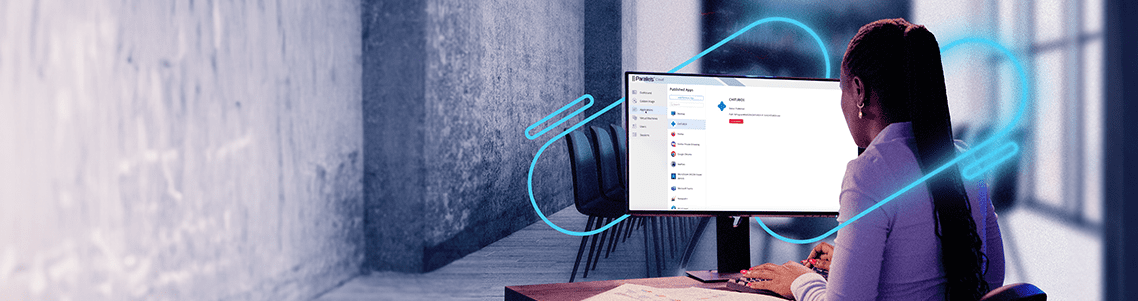
What is Parallels Browser Isolation (PBI)?
Parallels Browser Isolation (PBI) is a comprehensive, cloud-native solution that offers highly secure access to web applications and SaaS via a...
As more businesses use SaaS apps and the demand for remote work and the tools that facilitate it grows, online threats are increasing.
Traditional security methods...
As the Senior Vice President of Product, I am thrilled about the latest release in Parallels platform – Parallels Browser Isolation (PBI).
In this post, I’d like to emphasize the importance of Parallels Browser Isolation and how it...
The advantages of Desktop as a Service (DaaS) for MSPs.
As organizations strive to maintain operational continuity, optimize their resources, and secure sensitive data, Desktop as a Service...
DaaS is a cloud-based model where a third-party provider hosts and delivers virtual desktops to users. Unlike traditional VDI, which requires organizations to manage their own on-premises...